Security Information Management
Challenges for network security information management
Although most enterprises have deployed a firewall, virtual private network (VPN), ID authentication mechanism, intrusion detection system (IDS) and other technologies to guarantee network security, the propagation speed of network attacks may render the network substantially more vulnerable.
Different brands and types of network and security equipment have different management platforms and event databases. Where any network security event takes place, it shall be necessary to frequently log onto each unit of security equipment. However, logging onto one type of equipment only allows the user to check the security information of a particular aspect instead of the complete and general security conditions of the network. Moreover, the vast amount¬¬ of logs makes manual analysis an impossible mission.
Therefore, the No. 1 priority for an enterprise in deploying security equipment and applications on the network is to guarantee proper operations of the network in the optimal way. However, current security products are not normally able to prevent attacks and maintain network stability in the most efficient manner. For that reason, it is necessary to thoroughly change previous security information management concepts and models and establish new and scientific security information management architecture.
Security information management solution
Corporate security information management requires the availability of a uniform security information management platform that can monitor and control the multitude of logs and flow data generated by various types of security and network equipment, utilize various types of innovative technologies to simplify complicated network event information and only provide the network operators with the information necessary for monitoring and preventing network attacks. The system shall have the following features:
Remain updated with real-time security information and send prealarm messages promptly;
Collectively manage security equipment;
Rapidly identify the causes or virus sources/attack sources after a security event takes place;
Analyze data/event in a comprehensive manner and resolve the problems;
Establish a comprehensive security report.
Please see the following diagram for uniform security information management solutions:
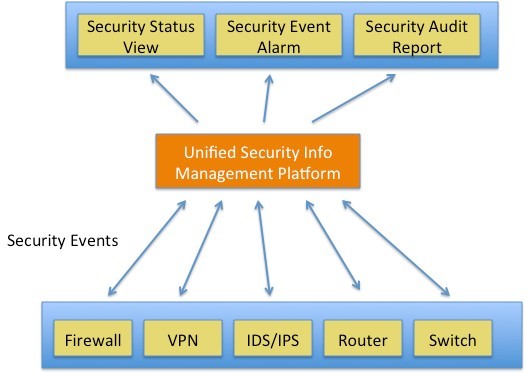
Conclusions:
A uniform security information management system can help an enterprise to collectively monitor, control and analyze network security events and to send prealarms against, locate, block and audit security events. It can improve the security management level and reduce the security-related operating and maintenance costs.
©Guangzhou Xinhua Times Data Systems Co., Ltd. 粤 ICP 备 09119233号-1