Access Control
Requirements
As corporate services and applications become fully dependent on network and computer terminals, there are more stringent requirements on the performance and reliability of network equipment, server and application system and a series of network security loopholes have emerged, e.g.:
Mobile equipment and new equipment are connected to the internal network without security inspections and security measures;
Internal network users conduct online dial-up Internet access, offline Internet access and other illegal behavior via MODEM, dual network cards, wireless network card and other network equipment;
Real-time, rapid and accurate positioning of the sources and remote isolation thereof are not conducted after virus and worm attacks and other security issues happen to the network;
The network administrator can’t locate the source of viruses or hack attacks and cannot identify the weakness of the network after a large-scale virus (security) attack happens;
IT administrators conduct operations in a willful manner. They are not properly certified, authorized and audited and can’t rapidly identify the source of problems.
Access control solution
Access control is an architectural design expected to guarantee the concerted operations of multiple types of hardware and software and protect the network from malicious attacks.
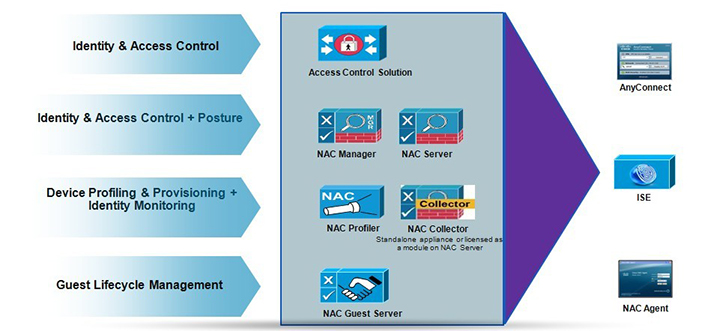
Through the integration of PC terminal software, RADIUS (or TACACS)-compatible network equipment, RADIUS (or TACACS) server, log server and auditing server, access control solution enables the collective management of network, host and desktop system and the event management procedure, release management procedure, configuration management procedure and service level management procedure in ITIL optimal practices.
Features realized:
PC access control;
Equipment automatic discovery and asset management;
Desktop security active evaluation;
Desktop security enhancement;
Illegal operation monitoring;
Software distribution;
Remote assistance, monitoring and control
©Guangzhou Xinhua Times Data Systems Co., Ltd. 粤 ICP 备 09119233号-1