Network Infrastructure Securit
Challenges for corporate network security
Corporate network security is not just limited within the borders of the network. The internal network also needs sufficient security protection measures. When the network is being attacked (whether the attacks come from inside or outside), the network infrastructures need to be sufficiently furnished to protect itself and trace and position the sources of attacks. In addition, different services may require different security levels. For instance, some business only require a firewall while others many require IPS/IDS or VPA protections. How can you establish a self-adaptive dynamic network security architecture that provides security services as per actual needs is a challenge that corporate network security faces.
Corporate network infrastructure security solution
Scope of corporate network infrastructure security
Corporate network security systems mainly involve the following aspects:
Network access security: the user must undergo authentication and security checks wherever they accesses the network so as to guarantee that all users and equipment connected to the corporate network are creditable. The typical solution is network access control.
Network security self-protection: all network equipment needs to enable logon authentication and flow attack protection. Network protocol (e.g. dynamic router protocol) also needs to enable authentication. All connected lines need to have QOS and other flow control features so as to prevent impacts of illegal data flows on essential businesses.
Security protection of essential IT assets: special security protections are needed for essential business servers and other critical IT assets, e.g. deployment of firewall, IPS/IDS, VPN and other security equipment. However, the entire security protection architecture must be self-adaptive and capable of dynamic and demand-oriented services.
Network flow monitoring and control: it can monitor and analyze network flows and protocol status on a real-time basis. When the network is being attacked, it can trace and locate the source of attacks. It can also provide basic data for network security strategy optimization.
Self-adaptive network security architecture
Traditional network security architecture is a serial architecture where all security equipment is connected in series for security protection. However, adjustment becomes very hard or extensively influential when security needs change. The schematic diagram of traditional network security architecture is as follows:
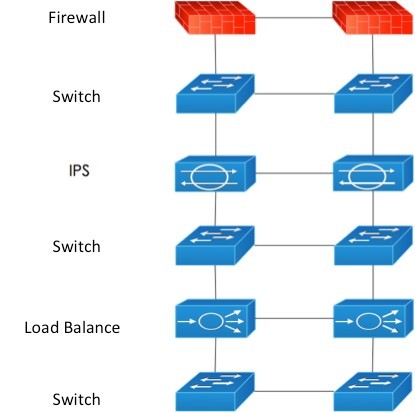
Figure 1
Self-adaptive network security architecture: establish an independent security service layer where all security equipment is deployed. Security services are launched according to the security requirements of different businesses. In addition, changes in security features are not going to affect current services. The architecture has a high degree of scalability and flexibility. The schematic diagram of self-adaptive network security architecture is as follows:

Figure 2
Conclusions
The borders of corporate network security protection not only are the exit of the external network, but also include the access layer of the internal network. Therefore, a well-established network security protection system must always have sound network infrastructure and all network access equipment must be capable of self defense. Meanwhile, it is also necessary to establish a self-adaptive security architecture that can integrate and launch corresponding security services according to the security requirements of different businesses.
©Guangzhou Xinhua Times Data Systems Co., Ltd. 粤 ICP 备 09119233号-1